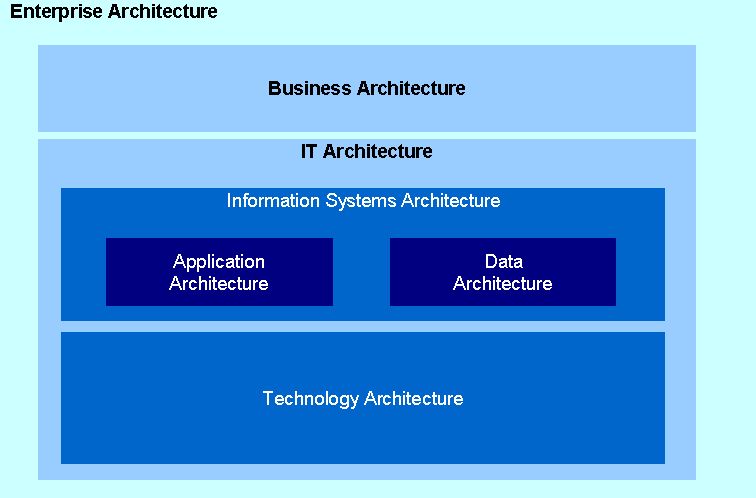
I was just listening to a podcast from Grady Booch on the difference between enterprise architecture (EA) and technical architecture (TA) and it got me to thinkng. In the podcast he defined EA as “attending to the architecture of businesses that uses technology” while TA “attends to architectures of software intensive systems which support that business.” He discusses the fact that the two subjects, except for sharing the word architecture, are separate and only slightly related. I don’t think this is entirely correct. I believe that TA is a subset of EA as shown in the following diagram, where Grady’s definition of TA maps to application architecture and technology architecture refers to the infrastructure components (semantics).
As he mentions EA defines the overall context of how technology is to be used within an organization to support the business goals of that organization. It is developed through the understanding and definition of the business architecture, the IS architecture and the technology architecture, each giving and taking inputs from the others. Thereofore, in my opinion, EA is not a discrete architecture one can develop, rather it is the sum of the other 4 domains.
He also mentions that not possible to extend frameworks, notations and processes of one area to the other. Again, since in my definition of EA, EA is not an architecture in itself but the superset of the other 4 domains, this makes sense. This is however also true to some extent between the 4 domains. Each domain deals with different viewpoints and therefore need to adopt the frameworks, notations and processes of their stakeholders. To use notations and processes of software developers in a business context will obviously not work. However, each does use a common vocabulary, such as viewpoints, stakeholders, etc. which does allow them to relate to one another.
By the way, loved his quote at the beginning of the podcast: “The more I know, the more I know I need to know and the more I know I don’t know.” Couldn’t be more true.