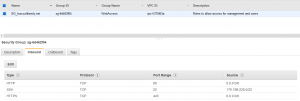
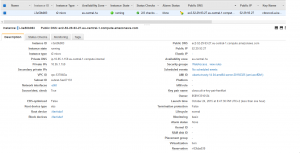
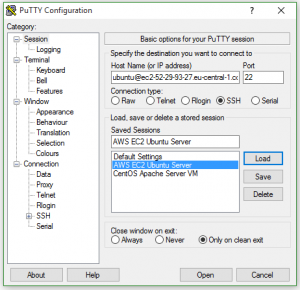
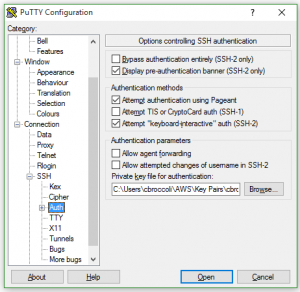
So once I was able to login with the default user (in my case ubuntu) I set about trying to setup a local personal user. Again Amazon provides some decent documentation under “Managing User Accounts on Your Linux Instance” but in this documentation they forgot one important step which I also could not find in the standard Ubuntu documentation.
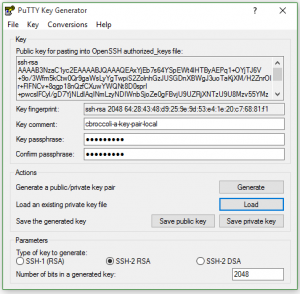
I setup the new user as described, added a .ssh directory under /home/username and then an authorized_keys file under that. I used puttygen to generate the public and private keys.
Using copy/paste, I copied the public key shown into the authorized_keys file.
ubuntu@ip-10-95-1-159:/home/cbroccoli-a$ sudo cat .ssh/authorized_keys ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEAxYjEb7s64YSpEWt4lHTByAEPq1+OYjTJ6V+9o /3Wfm5kCtw0Qr9gaWsLyYgTwpiS2ZolnhGzJUSGDnXBWgJ3uoTaKjXM/H2ZnrOIr+FlFNCv+8 qgp18nQzfCXuwYWQNt8D0sprI+pwcslFCyl/gD7YjNLdlAqINmLzyNDIWnbSjoZe0gFBvjU9U ZRjXNTzU9U8Mzv55YMzhz4MM5jQ++1xdj1qeJTtHWZt+SSKPW6To+q7D4IlNoK +irCV8L6CnvnPL0BvcuuXcuzhttnJ4Rwl6CbHft87n7blJb7tJAaQTtYV/SNGsz2oVr5Ytje O0Z8lDQmN/SKd+WY+Ft6I7uJw== cbroccoli-a-key-pair-local
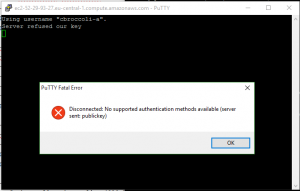
Finally I set the permissions to 700 on .ssh and 600 on the authorized_keys file. All as described. But when I tried to login, I got the error that the server rejected my key.
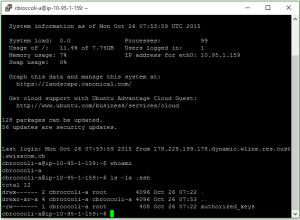
After some troubleshooting, I noticed the owner of the new .ssh directory and the authorized_keys file was root. So for both I changed the owner to the new user and that finally solved the problem.
ubuntu@ip-10-95-1-159:/home/cbroccoli-a$ sudo ls -la drwxr-xr-x 3 cbroccoli-a cbroccoli-a 4096 Oct 25 14:42 . drwxr-xr-x 4 root root 4096 Oct 25 14:28 .. -rw-r--r-- 1 cbroccoli-a cbroccoli-a 220 Oct 25 14:28 .bash_logout -rw-r--r-- 1 cbroccoli-a cbroccoli-a 3637 Oct 25 14:28 .bashrc -rw-r--r-- 1 cbroccoli-a cbroccoli-a 675 Oct 25 14:28 .profile drwx------ 2 root root 4096 Oct 26 07:22 .ssh ubuntu@ip-10-95-1-159:/home/cbroccoli-a$ sudo chown cbroccoli-a .ssh ubuntu@ip-10-95-1-159:/home/cbroccoli-a$ sudo ls -la total 24 drwxr-xr-x 3 cbroccoli-a cbroccoli-a 4096 Oct 25 14:42 . drwxr-xr-x 4 root root 4096 Oct 25 14:28 .. -rw-r--r-- 1 cbroccoli-a cbroccoli-a 220 Oct 25 14:28 .bash_logout -rw-r--r-- 1 cbroccoli-a cbroccoli-a 3637 Oct 25 14:28 .bashrc -rw-r--r-- 1 cbroccoli-a cbroccoli-a 675 Oct 25 14:28 .profile drwx------ 2 cbroccoli-a root 4096 Oct 26 07:22 .ssh ubuntu@ip-10-95-1-159:/home/cbroccoli-a$ sudo ls -la .ssh total 12 drwx------ 2 cbroccoli-a root 4096 Oct 26 07:22 . drwxr-xr-x 3 cbroccoli-a cbroccoli-a 4096 Oct 25 14:42 .. -rw------- 1 root root 408 Oct 26 07:22 authorized_keys ubuntu@ip-10-95-1-159:/home/cbroccoli-a$ sudo chown cbroccoli-a .ssh/authorized_keys ubuntu@ip-10-95-1-159:/home/cbroccoli-a$ sudo ls -la .ssh total 12 drwx------ 2 cbroccoli-a root 4096 Oct 26 07:22 . drwxr-xr-x 3 cbroccoli-a cbroccoli-a 4096 Oct 25 14:42 .. -rw------- 1 cbroccoli-a root 408 Oct 26 07:22 authorized_keys ubuntu@ip-10-95-1-159:/home/cbroccoli-a$
Now I can login with a unique user, using a private key that only I know and possess.