As the final NAC vendor, I decided to look at Juniper. At the end of 2011 Gartner posted their new magic quadrant report for NAC, which Juniper (who of course is in the Leader’s quadrant) kindly published for the general public (go to www.juniper.net if you would like a copy). Surprisingly, Cisco was also up in the leaders quadrant. Curiously, HP was not included in the report even though they seem to have a fairly well rounded solution. What I found most interesting about the report is the point that BYOD will be a driving force which may actually bring this wave of ANC products into the mainstream, something which to date, has not yet happened.
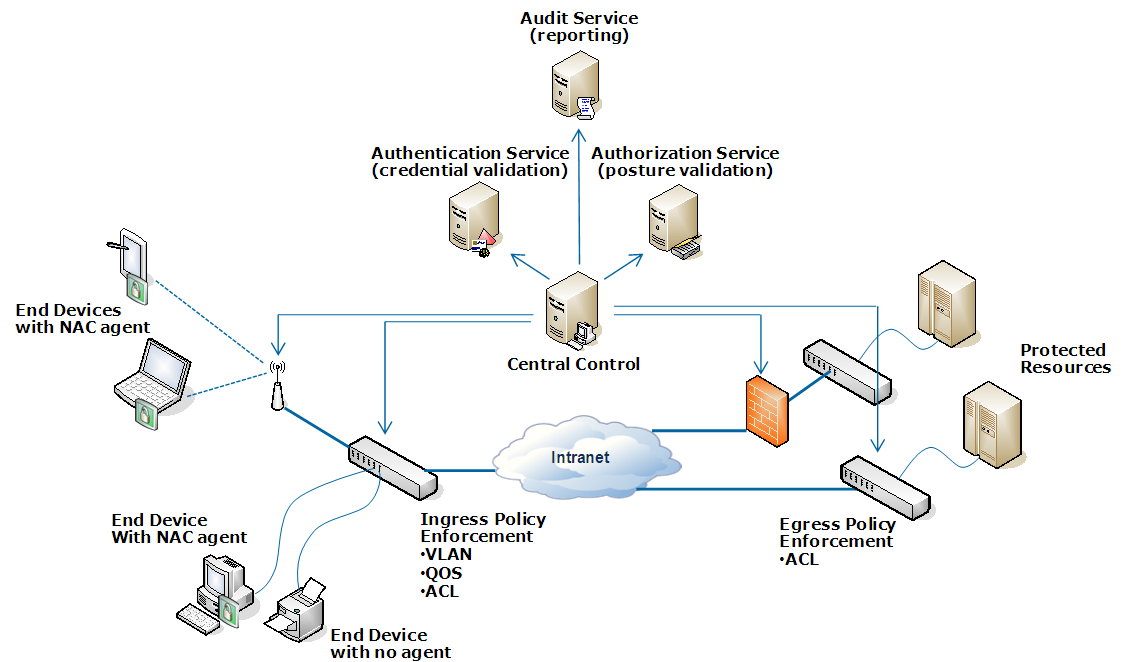
In looking at the Juniper model, and comparing it to the other two, it would seem that they all have converged on the same general architecture, even if the underlying protocols or implementations are different. The architecture is illustrated in the following diagram:
The central control system from Juniper is the IC series Unified Access Control appliances. These devices interact with layer 2 switches and AD to provide the dot1x authentication as well as Juniper secuirty devices (SSL VPN, firewalls) to provide the egress enforcement of the policies. From the literature, it looks however, like the system is not as dynamic as the ISE from Cisco. Policies are dynamically loaded onto the firewalls for egress filtering, but the policy is statically configured with the users IP address. So even if it is loaded dynamically, it needs to be set up in advance. Cisco applies the SGTs to the packets, which decouples the policy from the IP address, which is great.
Juniper does seem to support multiple NAC clients, including Microsoft statements of health. The Junos Pulse client is available for Windows with some other dynamic clients available for linux and MACs. There is a Pulse client for mobile devices (iOS, Android) but unfortunately this client does not support NAC for internal access. It is however an interesting product for mobile device managment and remote access vpn to an enterprises network. The MDM solution is a SaaS service provided by Juniper.
For a single management console, Juniper has their NSM (Network and Security Manager). This console allows the admin to manage the IC appliances from a central location where switches and other devices are managed from.